What is end-to-end encryption and why are tech companies focusing on it? Law enforcement organizations insist on encryption techniques that could allow for “lawful access by design”. But the messaging apps and internet behemoths seem to be making a stronger effort to adopt end-to-end encryption to secure more user data. Read here to learn more about end-to-end encryption.
Only the users who are conversing can read messages in an end-to-end encryption (E2EE) system.
In theory, it stops possible listeners from having access to the cryptographic keys required to decrypt the conversation. This includes telecom carriers, Internet service providers, hostile actors, and even communication service providers.
What makes end-to-end encryption unique compared to other encryption systems is that only the endpoints – the sender and the receiver – are capable of decrypting and reading the message.
Also read: Quantum Cryptography
What is end-to-end encryption?
End-to-end encryption (E2EE) is a secure communication technique that makes it impossible for outsiders to access data while it is transported from one end system or device to another.
- Only the intended recipient can decrypt the data in an E2EE transaction since it is encrypted on the sending system or device.
- The communication cannot be read or altered while in transit by an internet service provider (ISP), an application service provider, a hacker, or any other person, group, or service.
Many well-known messaging service providers, such as Facebook, WhatsApp, and Zoom use end-to-end encryption.
The adoption of E2EE has caused controversy for these providers. The technology possibly enables private messaging for those participating and makes it more difficult for service providers to provide useful information from their services to authorities.
How does end-to-end encryption work?
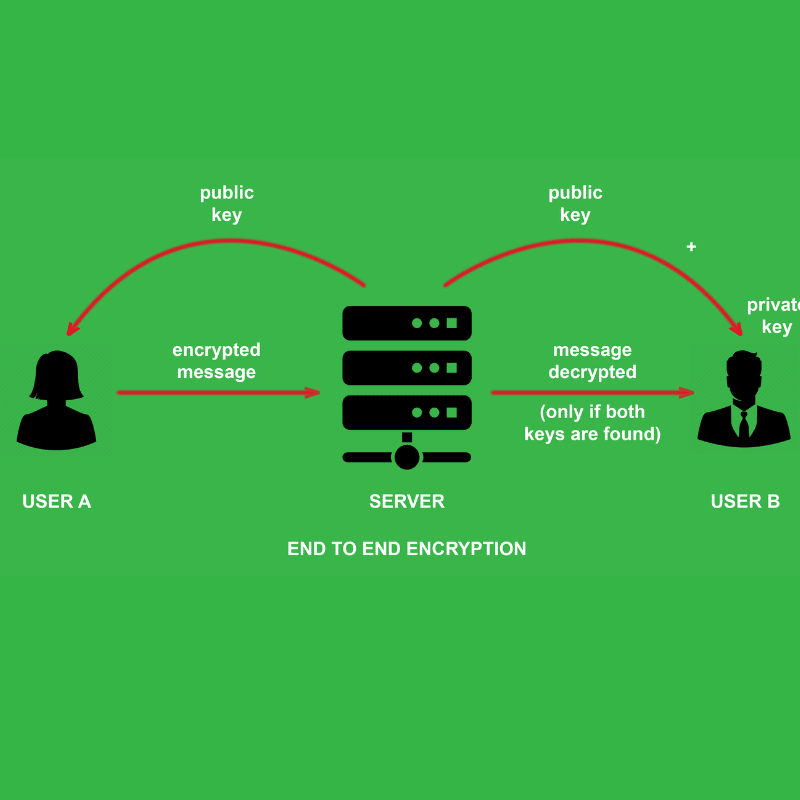
The endpoints hold the cryptographic keys that are used to encrypt and decrypt the messages. In this method, public key encryption is used.
- A private key and a shared public key are used in public key encryption, also known as asymmetric encryption.
- When the public key is made available, anyone can use it to encrypt a message and send it to the public key’s owner.
- Only the associated private key, also known as the decryption key, can be used to decrypt the communication.
Online conversations nearly always include a third party passing messages back and forth between the persons participating in an exchange.
- This middleman is typically a server owned by an ISP, a telecommunications provider, or several other businesses.
- The public key infrastructure that E2EE utilizes prevents middlemen from intercepting messages in transit.
Incorporating a public key into a certificate that has been digitally signed by a reputable certificate authority is the best way to ensure a public key is a genuine key generated by the intended receiver (CA).
- A certificate signed with the CA’s public key can be trusted because it is extensively used and understood, and because of this, its authenticity can be assumed.
- The CA would probably refuse to certify a certificate that linked a different public key to the same name because the certificate links the recipient’s name and public key.
How is E2EE used?
- When data security is required, such as in the financial, medical, and communications sectors, end-to-end encryption is used.
- It is frequently employed to assist businesses in adhering to data privacy and security rules and legislation.
- To protect sensitive data, such as consumer credit card information, a vendor of electronic point-of-sale (POS) systems might offer E2EE.
- The Payment Card Industry Data Security Standard (PCI DSS), which prohibits the storage of card numbers, magnetic stripe information, and security codes on client devices, can be complied with by retailers by using E2EE.
E2EE defends against these two dangers
- Prying eyes: Only the sender and intended recipient know the keys to decrypt the message, so E2EE prevents anybody else from accessing the communication’s contents in transit. The message won’t be readable, even though a server acting as an intermediary server and facilitating its transmission may be able to see it.
- Tampering: E2EE additionally guards against the alteration of encrypted messages. Any attempts to change a message encrypted in this fashion would be obvious because there is no way to predictably change it.
E2EE does not defend against
Even though the E2EE key exchange is thought to be impenetrable with current processing power and known methods, there have been numerous documented possible vulnerabilities of the encryption technique, including the following three:
- Metadata: While E2EE protects the information inside a message, it does not conceal information about the message, such as the date and time it was sent or the participants in the exchange. This metadata could give malicious actors with an interest in the encrypted information clues as to where they may be able to intercept the information once it has been unencrypted.
- Compromised endpoints: If either endpoint has been compromised, an attacker may be able to see a message before it is encrypted or after it is decrypted. Attackers could also retrieve keys from compromised endpoints and execute a man-in-the-middle attack with a stolen public key.
- Vulnerable intermediaries: Sometimes, providers claim to offer end-to-end encryption when what they offer is closer to encryption in transit. The data may be stored on an intermediary server where it can be accessed.
Advantages of end-to-end encryption
The main advantage of end-to-end encryption is a high level of data privacy due to the following features:
- Security in transit: End-to-end encryption uses public key cryptography, which stores private keys on endpoint devices. Messages can only be decrypted using these keys, so only people with access to the endpoint devices can read the message.
- Tamper-proof: With E2EE, the decryption key does not have to be transmitted; the recipient will already have it. If a message encrypted with a public key gets altered or tampered with in transit, the recipient will not be able to decrypt it, so the tampered contents will not be viewable.
- Compliance: Many industries are bound by regulatory compliance laws that require encryption-level data security. End-to-end encryption can help organizations protect that data by making it unreadable.
Also read: Virtual Private Network
Disadvantages of end-to-end encryption
Although E2EE generally does a good job of securing digital communications, it does not guarantee data security.
- Complexity: Some E2EE implementations allow the encrypted data to be decrypted and re-encrypted at certain points during transmission. This makes it important to clearly define and distinguish the endpoints of the communication circuit.
- Excessive privacy: Government and law enforcement agencies expressed concern that end-to-end encryption can protect people sharing illicit content because service providers are unable to provide law enforcement with access to the content.
- Visible metadata: Although messages in transit are encrypted and impossible to read, information about the message — date sent and recipient, for instance — is still visible, which may provide useful information to an interloper.
- Endpoint security: If endpoints are compromised, encrypted data may be revealed.
- Not future-proof: Although end-to-end encryption is a strong technology now, there is speculation that eventually quantum computing will render cryptography obsolete.
Encryption in India
There is no explicit encryption law in India. However, a number of industry regulations, including those controlling the banking, finance, and telecommunications sectors, include demands for the use of minimal encryption standards to secure transactions.
According to the licensing agreement between the ISP and the DoT, users are not permitted to use encryption standards larger than 40 bits utilizing symmetric key algorithms or comparable methods without prior clearance and deposition of decryption keys.
News about end-to-end encryption
- Apple has announced it will be increasing the number of data points protected by End-to-End Encryption (E2EE) on iCloud from 14 to 23 categories.
- In 2019, Facebook announced that all three messaging services would begin using E2EE. However, law enforcement and intelligence agencies argue that encryption limits Facebook’s ability to police illegal activity on its platforms. The debate often focuses on how E2EE can make it more difficult to identify and disrupt child abuse on private messaging platforms.
-Article written by Swathi Satish





Leave a Reply